Since World War II, the radar game between attackers and defenders has determined who will control the skies. The winner of the radar game gains the ability to bring the maneuver and firepower of air forces to bear against a foe or to deprive an enemy of this power. Highly survivable aircraft will contribute directly to achieving joint force objectives, and the ability to project power with efficient and effective air operations will depend on winning the radar game.
Aircraft survivability depends on a complex mix of design features, performance, mission planning, and tactics. The effort to make aircraft harder to shoot down has consumed a large share of the brains and resources dedicated to military aircraft design in the 20th century. Since the 1970s, the Department of Defense has focused special effort on research, development, testing, and production of stealth aircraft, designed to blunt the power of defenders to detect them and thus defeat or destroy them.
Stealth technology minimizes aircraft signature in several ways but most notably by greatly reducing its radar signature. Future plans for the Air Force F-22 and the triservice Joint Strike Fighter call for the nation to continue to procure advanced Low-Observable (LO) aircraft for the military. The Navy F/A-18E/F Super Hornet has a different and far more limited type of stealth. They mark the latest phase of the radar game.
For decades, the balance between the air attacker and air defender has shifted back and forth. However, invention of radar on the eve of World War II radically changed the balance of power in the air. During World War I, visual detection in daylight did not exceed 15 miles. Even in the late 1930s, defenders expected to listen and watch for attacking aircraft. By 1940, however, radar could spot incoming aircraft at a distance of more than 100 miles. Early detection gave defenders much more time to organize their air defenses and to intercept attacking planes. Radar height-finding assisted anti-aircraft gunners on the ground. Primitive airborne radar sets were installed in night fighters in the later years of the war.
Three Timeless Elements
In short, the radar game had begun. The game is about survivability. Elements of the survival duel emerged first during World War I, before the appearance of radar, and reappeared in World War II, Korea, Vietnam, and Desert Storm. There are three parts: detection, engagement, and probability of kill. Detection refers to spotting and tracking enemy aircraft. Engagement means fighters attempting to close with the enemy or ground-based defenses tracking and firing. Probability of kill means applying enough firepower not only to hit the other aircraft but to actually destroy or disable it.
The defender attempts to complete each stage. Without detection, no engagement is possible. Without engagement, there is no probability of kill. On the other hand, the attacker’s task is to thwart the defender at each stage. Ideally, the attacker would enjoy total surprise and arrive at the target undetected. If detected, pilots evade or prepare for engagement. If engaged, they seek to destroy or avoid enemy aircraft and to dodge enemy surface fire. If the aircraft is hit, probability of kill would depend on the nature and extent of the damage.
What is the payoff for signature reduction by means of a smaller Radar Cross Section? Achieving a lower RCS degrades the ability of enemy radar to detect, track, and engage aircraft. Lower RCS means aircraft are detected much later. A combat aircraft’s RCS varies with aspect and with the frequency of the radar attempting to track it. According to theoretical prin-
ciples, very low frequency radar waves may often be able to detect such aircraft. However, if RCS reductions are optimized to the higher frequencies of fire control radars, significant benefits can be achieved.
Lowering the aircraft’s observability to radar allows the aircrew to complete more of a mission before becoming vulnerable to radar-controlled weapons. This provides the attacker the advantage of avoiding the threat and minimizing the time in the “red zone” where detection leads to valid Surface-to-Air Missile shots. Also, stealth enables attacking aircraft to get closer to their targets. For example, shrinking SAM rings makes the SAM site and the targets it attempts to defend much more vulnerable.
For the purposes of this analysis, aircraft radar signature levels fell into five categories. Starting with the least advanced, they were:
- Conventional-no signature reduction and a large RCS.
- LO1 and LO2-levels of RCS reduction in the stealth zone but still not as low as aircraft may achieve.
- Very Low Observable 1-highly desirable and achievable RCS reduction.
- VLO2-hypothetical extreme not likely to be achieved.
- To simplify the data presentation, Figs. 510 portray each radar signature type only in the “mid-range” VLO1 form.
A Tale of Three Shapes
Combat aircraft in today’s inventory employ a number of different techniques for reducing their Radar Cross Sections, which are of three different shapes. The Fuzzball, Pacman, and Bowtie shapes are highly simplified symbols for basic signature patterns. Actual signatures are considerably more complex, of course, and information about them is restricted. The three shapes are used to depict how general patterns of RCS reduction give attackers a revolutionary edge.
 |
Fuzzball. A conventional, non-stealthy aircraft has a Fuzzball signature (Fig. 1), one which is constant from all aspects. Fuzzball is the ideal shape for a stealthy aircraft, with uniform reduction at all angles. It could in theory achieve remarkable results at the lowest levels. Theoretically, a perfect Fuzzball with a uniformly reduced cross section at -55 decibels would deny any radar return. However, a stealthy Fuzzball RCS is purely hypothetical and is used here only for illustrative purposes. | |
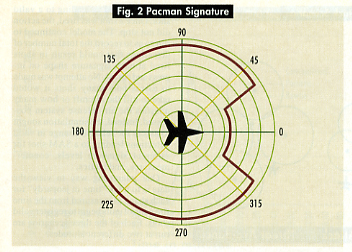 |
Pacman. This signature type (Fig. 2) is a simplified approximation of the RCS of a conventional aircraft retrofitted to reduce signature in the front aspect only. Within certain parameters, modifications can reduce RCS and improve survivability. For example, the Navy’s new F/A-18EF will emphasize front-aspect stealth. Applying Radar-Absorbent Materials to forward surfaces, shielding inlets, ducts, and canopies, and minimizing ordnance and other protrusions are some of the measures that can lower RCS from the nose-on angle. Rear and side aspects would not be reduced. Thus, in this notional case, a retrofitted aircraft might have a signature reminiscent of the creature in the early 1980s Pac Man video game. | |
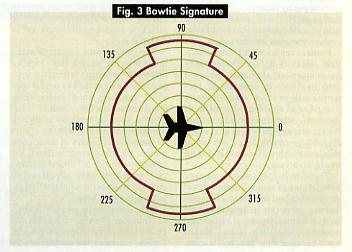 |
Bowtie. This hypothetical signature type (Fig. 3) is smaller in front and rear aspects than it is from the side. That would form something like a man’s bow tie. In simplified form, the theoretical Bowtie shape has a 15 dB reduction in RCS in its front and rear aspects. The Air Force’s F-117, B-2, and F-22 and the triservice Joint Strike Fighter are designed to be true stealth aircraft that are low observable from all aspects. Hypothetically, true stealth aircraft may achieve their smallest signature levels in the front and rear aspects. This might form a shape like a man’s bowtie. |
Stealth aircraft operations left the realm of computer simulations and training and endured the test of combat nearly a decade ago, in 1991. Air operations in Desert Storm illustrated that reduced RCS could indeed enable the F-117 to accomplish missions in air defense environments that would have been too hazardous for aircraft with conventional signatures.
The F-117s drew the most dangerous missions of the first night of the war. Iraq’s early warning radars, whose coverage reached well south of the border into Saudi Arabia, were designed to detect attacking aircraft as they approached Iraqi airspace. Sector operations centers would then coordinate tracks of the attackers, alerting SAM batteries and fighters as the mission profiles emerged.
As a postwar survey described it, these F-117s “flew into, over, and through the heart of the fully operating air defenses.” By doing so, they struck targets that weakened enemy air defenses and military command and control, with important effects for subsequent air operations.
Overall, the F-117s logged 1,297 sorties with no losses. With no attrition, the Joint Forces Air Component Commander was free to employ F-117s against any high-value target. As an official Air Force study concluded, “Throughout the war, they attacked with complete surprise and were nearly impervious to Iraqi air defenses.”
Duels of the Future
F-117 operations in Desert Storm demonstrated that direct attacks in heavily defended regions could be carried out by these LO aircraft. The record of the F-117s pointed toward many future applications for LO aircraft in the joint air campaign.
Future scenarios will not be identical. Heavily defended areas may have more air defenses than did Iraq in 1991. A number of scenarios will involve what might be described as a medium-threat environment, where a mix of mobile SAMs presents planners with a different type of challenge. On top of this, strike objectives of the future could also vary.
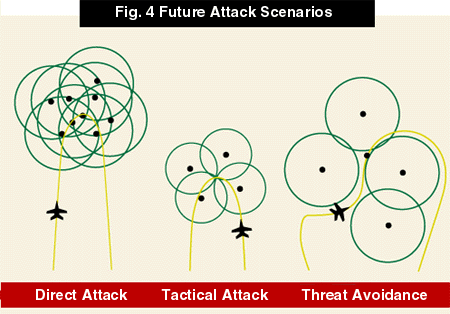 This article is based on results of simulations of three different threat environments of the future. The simulations were run to help illustrate how different signature reductions become controlling factors in aircraft survivability and in air campaign planning. These three scenarios were studied using a simplified version of a common air defense simulation model. Each environment mirrors the types of attacks that the joint forces commander may callon the air component to perform (Fig. 4).
This article is based on results of simulations of three different threat environments of the future. The simulations were run to help illustrate how different signature reductions become controlling factors in aircraft survivability and in air campaign planning. These three scenarios were studied using a simplified version of a common air defense simulation model. Each environment mirrors the types of attacks that the joint forces commander may callon the air component to perform (Fig. 4).
Direct Attack simulated a mission into a heavily defended region to attack a high-value target such as a command and control center or a weapons of mass destruction storage site.
Tactical Attack ran a simulation of an attack on a target that is part of a fielded military force.
Threat Avoidance featured aircraft flying a carefully planned route around known air defense sites to attack a time-urgent target in an isolated area.
The simulation itself employed a mission-level model that focused on events occurring within the integrated air defenses. The model captured variables such as the decisions made by the command and control system, the allocation and operation of SAMs, and the ability of the various radars in each component of the system to track the attacker and fire a valid shot. Several variables were simplified in order to extract the unclassified results presented here.
Simulated sorties produced a certain number of valid detections that could lead to the firing of a SAM. Graphs recorded the number of detections judged as leading to a valid shot. Once a shot was fired, the action did not stop. The model continued to run so as to record the total number of detections that could result in shots fired at each signature shape on ingress and egress. No attempt was made to assess how many shots it would take to kill the aircraft or how many missiles the air defense system possessed. Instead, the simulation sought to assess the relative change in valid detections leading to a SAM shot for different signature levels, countermeasures, and tactics.
One interesting way to view the data is to track “time in jeopardy” for each shape as measured from the time fire control units begin to register valid shots. Each of the three scenarios are run at two different altitudes.
Scenario 1. Direct Attack
The Direct Attack scenario posited an attack on a capital city in 2010. Key military targets are ringed with overlapping modern long- and short-range SAMs of a modern Integrated Air Defense System (IADS). The air defenses are generally positioned to maximize coverage. Only regions of major military importance are worth the investment of overlapping coverage. Where SAM detection rings overlap, coverage is so dense that it is intended to ensure a kill.
To attack, the aircraft must penetrate to its weapons release points even with threats from SAMs coming from all sides. The Direct Attack environment exposes aircraft to numerous radars, as would be expected in such an attack. In this most dangerous environment, a conventional aircraft signature suffers from both sustained, early detection and from a gigantic spike in detections over the target area.
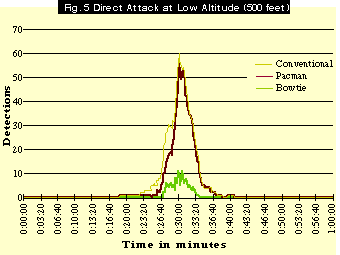 In Figs. 5 and 6, the yellow line corresponds to an attack mission flown by a conventional, non-stealthy aircraft at an altitude of 500 feet and 25,000 feet, respectively. Flying the mission at low altitude yields improved survivability, but not much.
In Figs. 5 and 6, the yellow line corresponds to an attack mission flown by a conventional, non-stealthy aircraft at an altitude of 500 feet and 25,000 feet, respectively. Flying the mission at low altitude yields improved survivability, but not much.
In Figs. 5 and 6, one sees how the Pacman shape performs in the Direct Attack environment, at both low and high altitudes. An aircraft with a Pacman signature, having only front-aspect stealth, fares only slightly better than the conventional shape. At low altitude, enemy detection of the Pacmantype aircraft occurs at about the same times as that of the conventional aircraft. At a point about nine minutes later, radar detections of the Pacman shape still number about 10, while the conventional shape has suffered about 30 radar detections. However, from that point on, the detection rates for both spike dramatically; Pacman suffers more than 50 detections over the target area.
Fig. 6 shows that, even at high altitude, the story essentially is the same.
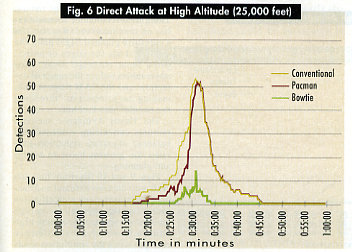 Pacman-type reductions would be of limited value to the campaign planner. Even when “nose-on” reductions put that part of the signature in the Very Low-Observable category, the number of engagements remains almost as for non-stealthy aircraft. The aircraft, as it flies away from the target, exposes large areas where its signature is not reduced.
Pacman-type reductions would be of limited value to the campaign planner. Even when “nose-on” reductions put that part of the signature in the Very Low-Observable category, the number of engagements remains almost as for non-stealthy aircraft. The aircraft, as it flies away from the target, exposes large areas where its signature is not reduced.
Aircraft having Pacmantype RCS would not have a good chance of completing the mission. Attrition rates would be high. This factor would make it difficult for the JFACC to count on sending such aircraft to attack heavily defended nodes. The JFACC would devise an air campaign plan that focused on rolling back air defenses prior to launching Direct Attacks of this sort.
Figs. 5 and 6, however, show that an aircraft featuring the Bowtie RCS shape, with significant all-around reduction, display a notable increase in survivability. The Bowtie RCS shape has two effects. First, the aircraft’s time in jeopardy diminishes. Second, signature reduction causes a drop in the number of valid shots. At low altitude, the aircraft spends only about seven minutes in jeopardy, compared to 23 minutes for a conventional signature shape in the same scenario. At high altitude, the figures are eight and 29 minutes, respectively.
Tactical advantages of Bowtie RCS are potentially enormous.
Front and rear aspect reduction, especially at lowest signature levels, greatly increases survivability against overlapping SAM coverage. The aircraft pounces on the air defenders, not even coming into the region of vulnerability until it is very near the target. Even over the target, defense radars record only about 10 detections at low altitude and 14 at high altitude.
Scenario 2. Tactical Attack
Tactical Attack is a scenario in which the air defenses are less dense but where numerous sorties will be flown either as part of peace enforcement operations or as part of wartime attacks on enemy forces in the field.
Some critical and demanding types of air operations entail attacking fielded military forces. In Desert Storm, for example, more than 70 percent of all sorties were flown in the Kuwait Theater of Operations in a tactical threat environment. The Tactical Attack scenario postulated an environment where forces on the move will bring along mobile, shorter range SAMs.
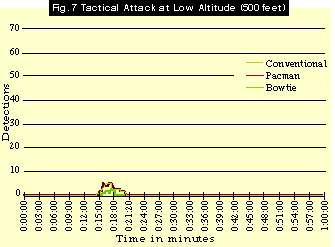 Fig. 7 lays out simulated radar engagement tracks corresponding to the three basic RCS types as the aircraft engage in Tactical Attack runs at low level-about 500 feet. As can be seen, such low-level attacks put great stress on mobile SAM operators. Even conventional, non-stealthy aircraft encounter relatively few radar detections. Pacman’s performance is not substantially different from conventional. The aircraft with the Bowtie RCS is hardly detected at all.
Fig. 7 lays out simulated radar engagement tracks corresponding to the three basic RCS types as the aircraft engage in Tactical Attack runs at low level-about 500 feet. As can be seen, such low-level attacks put great stress on mobile SAM operators. Even conventional, non-stealthy aircraft encounter relatively few radar detections. Pacman’s performance is not substantially different from conventional. The aircraft with the Bowtie RCS is hardly detected at all.
In Fig. 8, the yellow line denotes the simulated engagement track of a conventional aircraft shape at high altitude. Detections are fewer than in the environment of Direct Attack. Even so, the conventional shape is still fired on for a long time. The nose-on reduction of the Pacman shape keeps it from being detected until much later. Once inside a certain range, however, the Pacman’s large side and rear signature areas make the aircraft as vulnerable to radar tracking as a conventional shape.
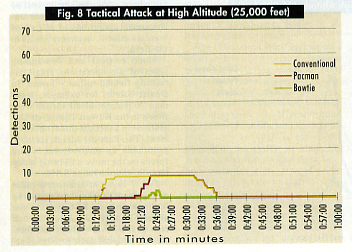 A major contrast is presented by the Bowtie shape. Its detection comes late, its vulnerability to air defense shots is minimal, and its time in jeopardy is brief.
A major contrast is presented by the Bowtie shape. Its detection comes late, its vulnerability to air defense shots is minimal, and its time in jeopardy is brief.
The evident lesson is that Pacman’s survivability advantages must be tightly coupled with the scenario. Nose-on RCS reduction of this type might be useful when an aircraft is part of a package performing lethal Suppression of Enemy Air Defenses to knock out fire control radars before turning to exit and exposing the large signature areas. Attrition risks will still be higher for the Pacman shape than for the Bowtie shape, but prospects for successful employment are improved.
Altitude is an important variable. In low-level attack runs, survivability improved for both the conventional shape and the Pacman shape. For the Bowtie shape, altitude does not make a significant difference.
Low-level operations bring their own kinds of dangers, however. Low-altitude runs face the danger of dense anti-aircraft gun threats. In Vietnam, over 85 percent of aircraft were lost to anti-aircraft fire. In Desert Storm, aircraft in the KTO reported sporadic dense anti-aircraft fire and shots from handheld infrared SAMs, even after the IADS had been reduced to almost zero effectiveness. The advantage of low-altitude missions–i.e., less vulnerability to radar detection–must be considered in light of threats from optically guided anti-aircraft fire, small arms fire, and handheld SAMs.
Scenario 3. Threat Avoidance
In the Threat Avoidance scenario, similar results emerge. This is another scenario in which an aircraft attacks a point target on a flight path that deliberately minimizes exposure to the fire control radars. The Threat Avoidance scenario relies on maximum use of tactics. In a carefully planned flight path, the aircraft skirts the edges of anticipated radar coverage areas. Low observables reduce the range of detection, and the SAM rings shrink, making the prospect of “threading the needle” much better.
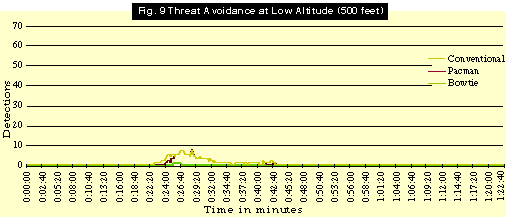
The Threat Avoidance scenario presents convincing evidence that balanced signature reduction provides the greatest boost to tactics and planning.
Figs. 9 and 10 illustrate that aircraft with the conventional and Pacman signatures, even with effective route planning, will still face a high number of shots at low and high altitude. However, a real difference emerges when the simulation sends in the Bowtie shapes. The VLO Bowtie signature aircraft showed enormous improvement in survivability, experiencing only one valid tracking.
 |
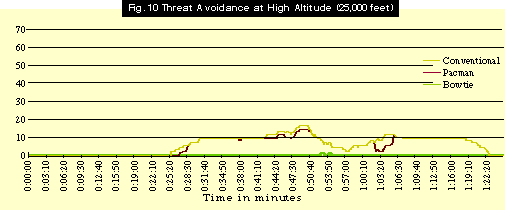 |
For the Pacman shape, what helped most was flying the attacks at lower altitude. Running the signature at low altitude minimized time in jeopardy and decreased overall shots taken.
The Threat Avoidance scenario confirms that significant low observables are essential to assured mission success. In Desert Storm, some targets could be attacked from low altitude by conventional aircraft. However, anti-aircraft fire was a factor; most attacks moved to medium altitudes as a result. British Tornados flew low-level attacks against Iraqi airfields and experienced some of the highest loss rates of the war.
The simulation showed that, as a survivability tool, going to lower altitude is not nearly as effective as reducing the signature. Moreover, the results suggested that flying at high altitude does not draw the aircraft out of the range of all SAMs, so stealth is important there, too.
However, the real message is that signature reduction enables the aircraft to plan a route that greatly increases the chances of survivability.
Stealth and ECM
The duels of the future may also draw on a combination of stealth and Electronic Countermeasures to improve aircraft survivability in specific scenarios. A conventional aircraft cannot operate safely in high threat environments until the integrated air defense is nearly immobilized. In theory, an extremely LO shape could be survivable in almost any environment. However, planning for the majority of air operations falls somewhere in the middle of that spectrum. As threat radars expand their capabilities, stealth and ECM have a role to play in working together to increase aircraft survivability-especially when prompt attacks on key nodes have reduced the efficiency of the enemy IADS.
In some scenarios, ECM can also provide additional assurance for LO aircraft against certain types of threats. While analysts have established that the F-117s did not benefit from ECM support from EF-111s on the first night of the war, records suggest that the additional use of the EF-111 was welcomed by F-117 crews in subsequent missions. For aircraft without the F-117’s signature reduction, or for aircraft operating in other environments, ECM can contribute significantly to survivability.
Conventional aircraft return much larger signatures. ECM is limited by the power of the airborne jammer. Therefore, a smaller aircraft RCS is easier to cloak because it requires less power from the jammer. An aircraft that reduces its front-aspect signature by a factor of 10 cuts the notional detection range by 44 percent. The power required in the ECM jammer also decreases in proportion. For the same amount of power, ECM can jam more effectively.
Improving Effectiveness
The first operational stealth aircraft, the F-117, and the B-2 demonstrated the feasibility of LO and their importance to rapid and effective air operations. Like all combat aircraft, they rely on tactics to reach peak survivability, and they have limitations that must be recognized to ensure proper employment. For example, the F-117 and B-2 operate primarily at night. Many conventional aircraft do the same to maximize survivability under some conditions.
Several developments will make highly survivable aircraft even more effective. The F-117’s ability to deliver laser-guided bombs was a crucial component of its effectiveness. Recently, the B-2 has demonstrated great accuracy with the GPSAided Targeting System
GPSAided Munition. Ability to deliver 16 independently targeted weapons in any weather represents a formidable improvement. In the near future, the development of small munitions will enable all aircraft to carry more destructive power. Testing is under way on 250-pound, 500-pound, and 1,000-pound bombs that pack the explosive force of the 2,000-pound bombs in today’s inventory. When stealth aircraft can deliver more munitions early in the campaign, they will take up an even greater share of the air component’s tasks.
With LO as the centerpiece, a range of technologies helps extend mission planning options and creates the tactical edge that translates to greater effectiveness and flexibility in air operations for a joint force commander. The F-22 not only will be able to achieve a dominant air-to-air role but also will be used as a highly survivable vehicle for delivering advanced air-to-ground munitions-munitions that could be used against SAMs or heavily defended targets. The trend toward development of smaller bombs will maximize the F-22’s internal carriage capacity.
Counters to Stealth
Because stealth is so important to current air operations and military strategy, it is reasonable to ask if and when it might be effectively countered. Historians contend that every military invention in history has been countered by new inventions or tactics, in due time. The radar game illustrates this principle, too. Radar changed the survivability duel during the Battle of Britain in 1940. Stealth changed it back fifty years later, in the Persian Gulf War of 1991. The most relevant question to ask is not “Can stealth be countered?” but “How difficult is it to counter stealth with known technology?”
To counter stealth with a monostatic radar, the air defense radar would have to greatly increase its gain at the receiver. The way to do this would be to greatly increase the power of the system. If the target aircraft had an RCS reduction of 1,000 the radar power would have to increase by a factor of 1,000 to detect it at the same range as a non-stealthy aircraft. However, increasing power is easier at long wavelengths-not at the short, rapid frequencies commonly used for fire control. Ultrawide band radar poses a similar problem. An ultrawide band pulse could emit waves at several different frequencies hoping to catch the stealth aircraft at a weak point in its RCS reduction. However, transmitting over a wide band diminishes the power in each band, cutting the efficiency of the radar.
The second issue in discussions of counter-stealth is that stealth aircraft are designed against monostatic radars, the type used in nearly all military systems. Monostatic radar couples the transmitter and receiver at the same place, a process that simplifies the crucial function of distance tracking. In theory, a bistatic radar that placed the transmitter in one location and the receiver in another might be able to pick up what might be called the “trailing” RCS that is directed away from the monostatic radar. However, bistatic radars, while simple in concept, have many fundamental technical and operational issues to overcome, according to John Shaeffer, RCS engineer at Marietta Scientific in Georgia. The receiver antenna beam must intercept its companion transmit beam and follow the transmit pulse which is moving at the speed of light. Unless the transmitter and receiver pulses are synchronized, distance measurement is impossible. Even a workable bistatic radar must then address the problem of how much volume of airspace it can scan at a given power setting in a given time. When the receiver, transmitter, and target are located on a straight line, the receiver can be overwhelmed by the transmitter pulse, which hides the target’s radar return. As Shaeffer put it, “This is similar to looking into the Sun for light scattered from Venus.”
The RCS reduction of stealth aircraft is difficult to counter. Improvements in radar must go a very long way to match the performance they were designed to achieve against non-stealthy aircraft.
Winning the radar game will remain central to American success in future joint operations. Air defense threats have increased throughout the 20th century and will continue to do so in the 21st century. Stealth is no magic panacea, but the edge it offers in the radar game is indispensable. Paired with other advantages from ECM to advanced munitions, the effects of LO multiply and will keep the edge of America’s airpower sharp.
Rebecca Grant is president of IRIS, a research organization in Arlington, Va. She has worked for Rand Corp., in the Office of Secretary of the Air Force, and for the Chief of Staff of the Air Force. Her most recent article for Air Force Magazine was “Khobar Towers,” which appeared in the June 1998 issue.